This article contains as much data privacy related information / advice as I could think to include with the goal of helping people better protect themselves in light of the gutting of Women’s privacy rights by the US Supreme Court. The vast majority of this information can apply to everyone.
This article covers many topics related to data privacy. Because this article is long – and I mean LONG … like over 10,000 words long – I’ve broken it into multiple sections that you can skip to easily using the table of contents below. Each section contains a link at the top allowing you to return back to the table of contents. While it is long, each section is important if comprehensive privacy is absolutely important to you.
Because of the amount of information I’ve attempted to fit into this single article, I cannot go completely in depth on any particular subject. I’ve provided as much information as I felt was absolutely necessary and link to additional articles on this site and elsewhere to provide more detailed information where necessary.

Original image from Blogtrepreneur used under the Creative Commons CC BY 2.0 license.
The first section of this article is meant to give you some idea of the scope of the ways at which your data privacy is at risk, followed in the next section with some basic information relating to encryption, a brief mention of data privacy laws that will help you better make the best decisions for how you improve your data privacy, and lastly relevant information regarding US law enforcement. After that it’s all actionable advice that you can use on topics like passwords, VPN services, web browsers, and more.
While this article is written with an American audience in mind, much of the information here should be useful to you regardless of where in the world you live.
Work through this information at whatever pace works best for you as there’s a lot to take in. Bookmark and come back if you need. Perhaps most important of all – please share this article with people you know and care about who can use it as well.
Lastly, if there’s something you think I’ve missed or got wrong or that you think I should consider including – PLEASE reach out to me with your suggestions. Leave your constructive feedback in the comment section, or if you prefer you can easily reach me via one of my social accounts.
Table of Contents
You’re Being Spied On Every Day
We’re all familiar with the joke – and you know that it’s true – if you start talking about something in the presence of your phone or a smart speaker you’re bound to start getting ads and content recommendations about whatever it was you were talking about.
Devices like cell phones, tablets, and your car – if it has OnStar or built in navigation – has the ability to be tracked using GPS – often with the data being recorded. People are even using Apple’s AirTags to track other people instead of their lost property.
Interjecting here quick to point out that there is reporting that Google is going to remove visits to places like abortion clinics, among others, from any location data they collect. Check out the linked article for additional details as well as information on how Apple handles location data.
The vast majority of operating systems found on the devices you use every single day collect telemetry data that gets transmitted back to the OS developer – Microsoft, Apple, and Google are all guilty of this. When you first setup your Windows PC, you have the option to disable much of the data collection that Microsoft does – and while you can go back and opt-out after the fact we aren’t entirely sure what data is actually collected or not – we have to take Microsoft’s word on it.
Apple has carefully crafted an image of being sensitive to people’s data privacy over the years – “What happens on your iPhone stays on your iPhone”, for example – however, they aren’t perfect when it comes to their data privacy record. For example – every year Apple is paid upwards of $15 billion by Google just to remain as the default search option on Apple products.
It was reported in 2020 that in 2018 Apple backed down from a plan to encrypt iCloud backups due to objections raised by the FBI that it would hinder investigations. While Apple has on multiple occasions remained publicly steadfast about unlocking the actual devices of users for governments, they have willingly turned over those iCloud backups.
Apple eventually did reverse course on this decision and does make available the option to enable encrypted backups from iOS devices.
Google abandoned their once famous motto, “Don’t Be Evil”, years ago now. The search giant collects data on everything you search about, they probably created the browser you’re reading this with – Chrome – which gives them access to data about what you do online, they hold a virtual monopoly in the online analytics world (find me an advertising network that doesn’t require you use Google Analytics … I’ll wait), they run Gmail – one of the most popular free mail services in the world – and YouTube, and the list goes on. Google likely knows more about you than anyone else including your significant other.
If you need any reminder of just how nefarious Facebook can be with regards to data and its platforms, set your wayback machine to the 2016 election and a company called Cambridge Analytica and how Facebook was aware of how their algorithms use data to steer people into right wing extremism.
There’s been recent reporting (as of the time this article was published) that TikTok user data from the US has been repeatedly accessed in China – something they promised wouldn’t happen.
Even smart TV’s have been used to collect data on consumers. In 2017 for example, Visio was hit with a $2.2 million fine for using image recognition to monitor what people would watch on their TVs in order to sell that data to others.
Facial recognition technology has advanced to the point where concerns for the potential of its abuse caused many big tech players to stop selling the tech to law enforcement agencies.
The camera in your phone or laptop can be made to spy on you without your knowledge – something that has led many laptop and webcam makers to equip their devices with privacy shutters to put consumers at ease that they’re not being watched.
I haven’t even mentioned anything about the loyalty card you use to earn points toward discounts at the grocery store and how the data gathered from these builds profiles about what kind of things you purchase nor how hackers love collecting your personal data so they can steal your identity, sell your information on the dark web, or even use it to scam other people you know.
For as many ways that I mentioned above on how you’re being spied on every day, it was by no means an exhaustive list. It’s not my intention to scare you, but to show you just how prevalent the threat is to your data privacy.
Important Information
It’s important to have an understanding of a few concepts before we get into ways you can try to improve your data privacy.
Encryption
The first concept I want to address is encryption. Don’t worry – I’m not going to make this a particularly technical discussion. A minimal comprehension is all that’s required to help you better understand the data privacy advice in this article.
Let’s start by defining encryption. Encryption is converting information into a secret code that can’t be read without the required key that decodes it. Any further explanation is likely to involve a math discussion that neither I nor you likely want to get involved in.
There are a few terms encryption related terms that you should be aware of as well.
Data-At-Rest / Data-In-Transit
Data-at-Rest refers to data that is encrypted when stored on a device. You might encrypt a hard drive of a computer or even your phone so that nobody without the required password can decrypt the data on those devices. In this situation, the password acts as your decryption key.
Data-in-Transit refers to data that is being sent across some communication channel like wired and wireless networks. Another term you’ll run into that’s related to this is end-to-end encryption. When you see any discussion of these terms, it means that the data being transmitted is encrypted at the sending end and decrypted at the receiving end so that anyone who might intercept the transmission can’t access the data.
As you’ll hopefully see by the end of this article – when it comes to protecting your data privacy, encrypted technologies are the key to nearly everything.
Data Privacy Laws
Let me take this opportunity to be clear that I am not providing legal advice and I do not claim to be any kind of legal expert. You should always conduct your own research or speak with an attorney if you need legal advice.
Next, I want to make you aware of data privacy laws that you can take advantage of. In recent years, California has passed their Consumer Privacy Act and nations such as the European Union(EU), Switzerland, and others have passed a number of laws governing how the private data of their citizens must be handled by third parties.
California
The California Consumer Privacy Act (CCPA) was implemented to protect the data privacy of California residents, specifically. If you live in California you should make yourself familiar with the rights it grants you.
Outside the US
Data privacy regulations in countries other than the US, such as GDPR in the EU, and the many privacy related laws in Switzerland are considered to be much stronger than California’s regulations. Residents – not citizens – in these areas should also avail themselves of their rights granted by their respective laws.
I’ve mentioned Switzerland in specific in this discussion because it’s generally considered to have the strictest data privacy laws. As a result, many privacy oriented services have incorporated themselves in Switzerland to take advantage of these laws.
In general, Switzerland is reluctant to transfer data to third parties in countries without strong protections for privacy with an exception for corporations that have come to acceptable contractual agreements with regards to privacy.
When it comes to law enforcement requests, there are international treaties that allow for obtaining data stored in Switzerland. When searching for an explanation of how this process works, I happened upon a page specific to this purpose from one of these privacy focused corporations.
Proton (you’ll see them mentioned multiple times as you continue on) was kind enough to include an easy to understand explanation of how law enforcement requests work in Switzerland on their website. To summarize the relevant highlights – all requests from law enforcement agencies require disclosure to the subject of the request and will be heard by Swiss authorities for a determination of whether the data request will be made.
Because of their strong stance on data privacy, services based in Switzerland should be given the most serious consideration when evaluating ways to ensure your private information.
US Law Enforcement
The last thing I want to discuss before we get into strategies is information related to what US law enforcement can and can’t make you do with regards to your devices based on the latest available information I was able to find.
Can police Make you unlock your devices (phones / Laptops)?
Police accessing your phone or device is considered a search under the 4th amendment and compelling you to unlock a device is a violation of your 5th amendment rights against self incrimination.
In general, police can only search anything on your person in 4 circumstances:
- You consent to a search – NEVER DO THIS
- They have a warrant
- Probable cause
- You’re under arrest
This article from Android Authority does a good job of giving you the basics on what to do if you end up in one of these situations. For that matter, they cover these sorts of issues really well, in general.
Exception – US Customs & Border Patrol
The exception to the rule regarding searching your devices you have on you is if you’re crossing a border or entering/exiting the country in any way. You’re not without options here but the likelihood of you leaving without your device increases if you refuse to let them search it if asked. I highly suggest reading the articles I’ve linked here for additional information.
Passwords & Authentication
Let’s begin with your first line of defense against unwanted violations of your data privacy … passwords and authentication methods. This should go without saying – the more difficult you make it to access your data, the more secure it is. Improving your passwords is something you can do today, immediately, without having to spend any money, and gain a substantial improvement to your data privacy.
Use Strong Passwords
I’ve mentioned this chart in another article on Enforcing Strong Passwords In WordPress and I’ll likely mention it again somewhere else because it’s that good at getting the point across about password complexity.
Every few years, Hive Systems releases an updated version of this chart showing the maximum – not minimum – amount of time it would take someone to crack a password using only a desktop computer with a top-of-the line graphics card (they’re great at this kind of math) – no servers or supercomputers required, though, if more serious compute power is used, these numbers decrease quickly. This version of the chart was released in March 2022.
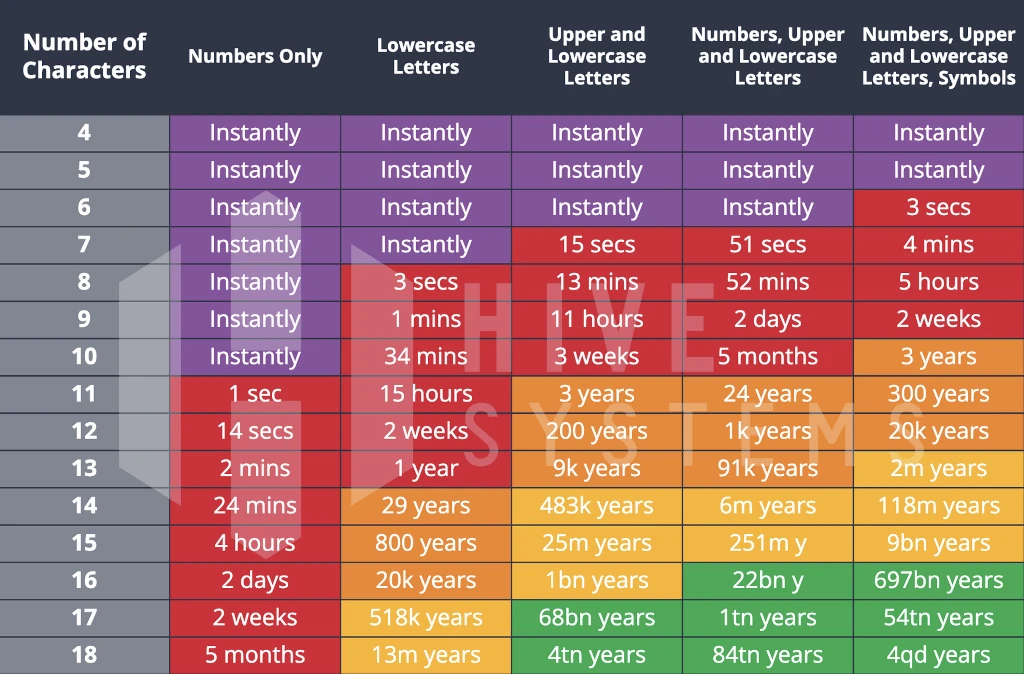
What to take away from this chart – the longer your password is and the more kinds of characters it contains (numbers, uppercase, lowercase, symbols) the longer it takes for someone to crack it. My personal suggestion is at minimum use 14 characters with uppercase, lowercase, and numbers. Longer and including symbols is better. This is especially true for protecting your phones and other mobile devices as there aren’t any options I’m aware of for adding a second factor of authentication to these devices.
UPDATE – apparently, if your phone supports it you can use a NFC enabled hardware security key like the Ubikey I link to below as a two-factor authentication method. Extremely useful info! Thanks to @artcspgs on Twitter for pointing this out.
Two Factor Authentication
Anywhere you have the ability to enable two factor authentication to an account – do it. There are numerous apps available to use on your phone for both Android and iOS – Google Authenticator, Authy, Lastpass, and Microsoft Authenticator amongst others.
Enabling two factor authentication, for those who aren’t already aware, is a secondary requirement to logging into an account besides your username / password combination – usually a series of numbers that changes every minute or two.
Not All 2FA Methods Are Safe
The better options for two factor authentication is using an app like I mentioned above or using a hardware security key as I’ll talk about shortly. Many places, however, are still using codes sent via SMS or email as two factor authentication methods. THIS IS BAD.
SMS is inherently unsafe because SIM swapping is not incredibly difficult to pull off. Once someone has accomplished this, they will now receive every phone call and text message that should have gone to your phone.
Similarly, if someone manages to access your email in one way or another, they can wreak havoc on any account that uses it without a separate system for authentication.
Hardware Security Keys
Many organizations are beginning to support an authentication system called FIDO that allows you to pair a relatively expensive hardware security key, such as a Ubikey (affiliate) or TrustKey (affiliate), to your accounts. With a hardware keys configured as a requirement for access to accounts, nobody will be able to access your accounts without one of the authorized keys.
Hardware security keys can also be used as a two-factor authentication device for your desktop PC – whether it runs Windows, MacOS, or Linux.
Problems With Pin numbers
I hope this is obvious after the password cracking chart, but … securing your device with a pin instead of a password, while convenient, is not going to keep someone determined from getting access. There are too few combinations of digits to effectively protect your device even if someone doesn’t know your birthday or the last 4 digits of your SSN – both are popular pin options because people remember them. Don’t use these as pins, ever.
Problems With Biometrics
Biometric login options have become popular in recent years for phones and laptops, however, I caution against their use if you are serious about your data privacy / security.
While law enforcement isn’t supposed to force you to unlock your devices with your fingerprint or face ID, there are lots of things law enforcement isn’t supposed to do that they do anyway. Anyone else interested in accessing your devices might also attempt the same sort of thing.
A somewhat silly example but this illustrates my point – I once woke up because my kid, who at the time was 5 yrs old, was attempting to unlock my phone with my face while I was asleep because he wanted to put on YouTube videos. After this, I removed the facial recognition from my phone.
Lastly, while Apple claims to have overcome this problem – back in 2017 researchers were able to fool the iPhone’s facial recognition with a 3D printed mask. I’m sure this won’t be the last time someone figures out a way to get past this kind of system.
App Permissions
It’s not unlikely that at some point you’ve installed an app to your phone or tablet without giving much thought to the permissions you’ve granted it. It’s not a bad idea to periodically remove apps you’re seldom using for this very reason. Additionally, you can review and modify the permissions of your apps – both for Android and iPhone – at any time.
Pay special attention to which apps want access to things like your microphone, camera, location, contacts, and SMS messages. Don’t be afraid to be strict about app permissions if you need to be. You can always adjust them again later.
Period Tracking Apps
The entire inspiration of this article was the recent Supreme Court decision that killed women’s rights / body autonomy. With reports that many Republican led states that have already banned abortions now looking to prosecute women who travel to other states to obtain one, there are serious concerns about places where they might turn to for evidence to use in prosecution.
Problematic Apps
One of these places is apps that women use to track their menstrual cycles. It seems many such apps collect data on the users that could be subpoenaed for use in prosecution.
Serena DiPenti, a TikToker and pen-tester that I follow on Twitter, has published at least a dozen videos with regards to some of the various apps that are out there and their shortcomings. I highly recommend you watch them if this issue is important to you.
I will call out one specific app to avoid as it’s one that has given people the impression that it’s safe while people like Serena have evidence to show that it in fact is not. That app is called Stardust. Problems with this app were first pointed out by a team of people at TechCrunch. If you’re interested in why you should avoid this app in particular, I suggest reading their reporting as well as watching Serena’s videos.
UPDATE 2022-07-06: The Stardust app has been removed from the Google Play store.
Recommended Options
If you’re going to use an app for this purpose, here is a short list of recommended apps. Again, credit to Serena for these recommendations.
Android / iOS coming – Drip
The Drip app is open source software that runs entirely on your device without transmitting data elsewhere. If you’re an Apple device user, their website has a form that can email you when the iOS version of the app is available.
iOS – Spot On Period Tracker
If you decide to use the Spot On app, according to Serena there are two things you need to be aware of. 1 – be certain to skip account creation. Doing so will cause all data to only be stored locally on your device instead of transmitted to Spot On. 2 – Spot On has a link to additional resources on abortion and healthcare access in the app. Clicking this link takes you out of the app to their website where you could potentially be tracked.
iOS – Health App
While the Health app won’t be as fully featured for this use as other more specialized apps, Apple encrypts all of your health data on your device and you can additionally enable encryption for iCloud backups as well. See the section below about encrypting your device for more information.
Secure DNS Providers
Simply put, DNS is what makes the internet work. It translates your easy to remember domains, like techaddressed.com, into an IP address that allows devices to actually request and receive information.
The average person never gives any thought to DNS or who is providing them DNS services – typically their ISP or mobile data provider. So … if I’m mentioning this, there must be a reason, right? Right.
Whichever DNS servers you’re using log every DNS query you make to the servers. Those server logs can tell anyone who has access to them every domain has requested data from your account. If logs exist, those logs can be subpoenaed.
Until recently, all DNS requests on the internet were transmitted unencrypted. Anyone in theory could monitor network traffic and see what requests were being made. To combat this, a pair of technologies called DNS-Over-TLS and DNS-Over-HTTPS (collectively referred to as Secure DNS) which encrypt all DNS requests made to your DNS provider. (I previously wrote an entire article titled “DNS Over HTTPS: Everything You Need To Know” that you can refer to for a more detailed explanation as well as instructions on how to modify these settings in most browsers.)
All of the most popular web browsers support this technology – most have it enabled by default. You can refer to my aforementioned article for instructions to help you check / modify your browser’s settings. The only browser that requires a special mention here is Firefox – who by default, regardless of your device’s DNS settings, sends all DNS requests to Cloudflare’s 1.1.1.1 DNS service. If you use Firefox and plan to use a different DNS provider than Cloudflare, you’ll need to be sure to modify the settings.
While browsers all have this technology enabled, your computer or other device may or may not. Windows and MacOS both have support for the technology but it’s not necessarily enabled by default.
If your typical DNS provider’s server logs all of the requests made, however, your activity online can still be tracked in this way. The solution is to change your DNS provider to one who actually respects your privacy.
Recommended Options
I have only two recommendations here. One hosted by someone else and one you host yourself.
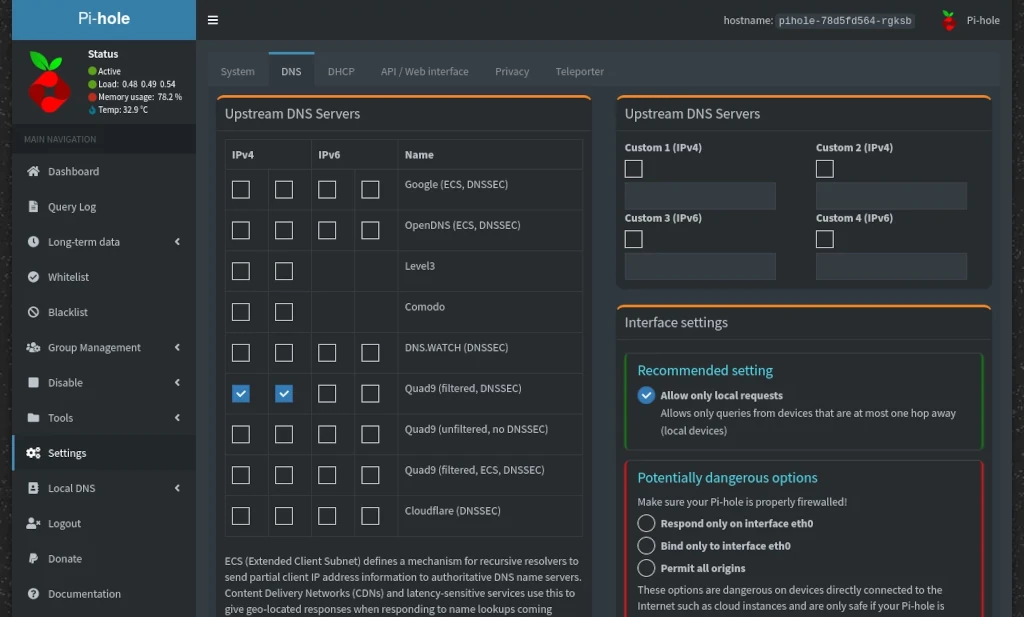
Quad9
Quad9 is a not-for-profit organization – based out of Switzerland – with servers at 150 locations in over 90 countries. Their servers are free for anyone to use – no sign up or user account information of any kind is required. Quad9 neither stores nor transmits IP addresses of users and being a non-profit it has no need for a revenue stream from selling personal data or up-selling you on additional services. Additionally, being based in Switzerland means they are subject to their strict data privacy laws.
In addition to improved privacy, Quad9 also offers your devices protection by blocking threats from your system from malware and phishing sites. With Quad9, when your device makes a DNS query the domain is compared against a list of threats compiled from intelligence partners and completes the request based on whether there’s a match.
Quad9’s servers can be used by any device and operating system. I’ve linked below to resources on setting up your devices for Quad9.
Setting up Android or iOS following the linked methods enables secure DNS without any extra steps, however this isn’t the case for Windows or MacOS. Here are additional resources for checking / enabling secure DNS on Windows and MacOS.
When configuring iOS using the linked instructions, you have the option to enable logging your DNS queries. This is entirely up to you but keep in mind – if you log information to your device it’s evidence of where you’ve gone online.
Run Your Own DNS Server With Pi-hole
If you’re more technically inclined or just prefer having as much control as possible over your data privacy, you have the option to setup your own Pi-hole instance on your home network and configure it as a recursive DNS resolver. I have an entire series of pi-hole articles already on how you can do this.
Running a Pi-hole instance comes with the additional benefit of being able to act as an ad-blocker for every device on your network. Not only does it block ads, but it also does a good job of shielding you from trackers like Google Analytics. The software is open source, so if you have a spare computer or a Raspberry Pi device handy, it’s a worthwhile project to consider giving Pi-hole a try.
VPN Services
In recent years, VPN services have become popular for a number of reasons. Most often they’re used by the general public to circumvent geographic limitations to accessing online media – for example watching USA only Netflix content from Europe.
Because of how VPN services have been marketed, however, people also often think that a VPN will solve their online privacy issues and completely hide them from being tracked online. Nothing could be further from the truth. A VPN absolutely can be a useful tool in ensuring your data privacy, it is not a one-stop-shop solution.
What A VPN Actually Does
A VPN – or Virtual Private Network – does just one thing. It makes your internet traffic look like it is coming from somewhere you’re not. Say you’re located in Atlanta and you connect to a VPN server in Chicago, your public IP address won’t be your actual home IP but the IP of the VPN server in Chicago. Any servers you access will log your IP as such.
The data you send through the VPN is encrypted between your device / network (depending on whether you’ve added the VPN to just your device or to your entire network) and the VPN endpoint where it exits into the public internet.
Every cookie and tracker that you access still knows you are you – you’re just fooling them into thinking you’re somewhere else.
Hiding your location is definitely useful – just remember it’s only one piece of the data privacy puzzle.
Not All VPN Services Are Created Equal
The major problem with VPN services is that you’re forced to trust whether or not they’re logging your online activity. While most will claim they don’t keep usage logs, you really don’t have anything tangible to rely on that this is the case and are forced to accept their word on the matter. There are a couple rules you can use, though, to help guide you in this decision
- Is this service free?
- Where are they headquartered?
The old maxim that “if something is free, you are the product” is usually correct. Unless they have other products / services that generate income to offset the cost of a free service, I would expect most free VPN services to be collecting data on its users to be sold.
Recommended Options
As I discussed earlier in this article, organizations based in countries with strong data privacy laws are more likely to take your data privacy seriously. With that in mind, I went out and found a couple of VPN providers based out of Switzerland – again they have the strongest data privacy laws – to recommend here.
Proton VPN (Affiliate)
Proton (affiliate) provides a number of privacy focused services – we’ll discuss a few more of them later in this article – and is regarded by many as one of the best choices for a trustworthy VPN service – the service was started with the goal to help protect the privacy of journalists and activists.
Proton DOES have a free service available – likely the only free VPN service I’d consider trustworthy – as well as paid options and has support for basically every device and platform imaginable.
Additional features that Proton offer with their service include the ability to enable ad-blocking via their NetShield DNS filtering system – basically it’s like having a Pi-hole without having to run a Pi-hole – and the ability to use the Tor anonymity network through the VPN connection. Tor is discussed later in this article.
VyprVPN (Affiliate)
VyprVPN is another provider with a heavy emphasis on privacy rights – founded as a response to help prevent government surveillance and ISP tracking. Like, Proton, VyprVPN offers a DNS filtering service to help protect you from being tracked online. They also feature a kind of kill switch that prevents any traffic to or from your device when it’s not connected to the VPN service.
In an effort to show their commitment to privacy and openness, VyprVPN commissioned a full independent audit of their systems to certify their systems keep zero logs. They additionally claim to be the only VPN provider that owns 100% of their equipment instead of leasing server equipment from third party data centers.
Further, they contacted the Center for Democracy and Technology – an organization with the goal to “strengthen individual rights and freedoms by defining, promoting, and influencing technology policy and the architecture of the internet” – to request the creation of an independent vetting process and standards for VPN companies in hopes of improving the privacy standards of the entire industry.
Web Browsers
So much of what we do on computers today is done through a browser. In the 90’s, Bill Gates was rightfully worried about how they could threaten Microsoft’s Windows monopoly. With how important browsers are to how we work and communicate with the world, it’s important to examine how they affect your data privacy.
Understanding Incognito / Private Window Mode
It’s not uncommon for people to misunderstand how their browser’s incognito mode / private window mode works. Many assume that these modes provide some kind of active protection similar to how a VPN works, however, nothing is further from the truth.
When you open a webpage using incognito / private mode, the differences when compared to your normal browser is that you’re not logged into any of your otherwise logged in accounts, it cannot access any cookies that are otherwise tracking you in your normal browser, and any cookies stored in the private mode along with the browser history generated while in private mode are deleted when the incognito / private window is closed.
This doesn’t prevent any sites you visit from knowing your IP address – potentially allowing sites and any trackers running on them to recognize who you are. The only thing that really remains private about these browsing modes is that your activity doesn’t show up in your browser history – great, maybe, for hiding what you do online from others in your home but on its own, it won’t do much to protect you from being profiled online.
Do Not Track
All browsers should allow you to enable a setting called Do Not Track which is used to request that websites do not track your browsing activity. The problem with this signal from your browser is that it is merely a request and can simply be ignored. It’s worth enabling the setting for anyone who’ll honor it, but don’t rely on it as your only solution.
Recommended Options
There are a only handful browsers that I can recommend that take your data privacy seriously.
Firefox
Of the mainstream browsers – mainstream meaning people in general have likely at least heard of it – Firefox is the only one that I can stand behind in any way. Firefox includes a number of privacy focused features that separate it from the others.
Firefox includes settings for “Enhanced Tracking Protection” – by default blocking things like social media trackers, cross-site cookies, cryptominers, and fingerprinters, and any tracking content in private mode windows. Switching the setting from Standard to Strict blocks tracking content in all windows, not just private mode.
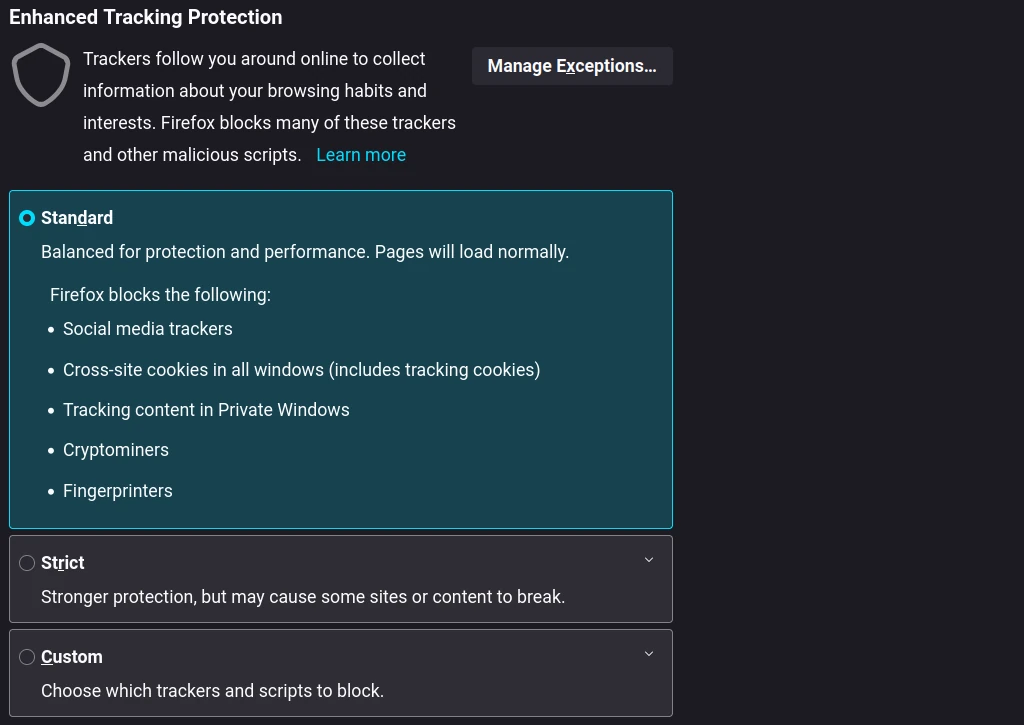
With Firefox 102 (released days before this article was published), they introduced another feature to the Strict setting that strips out tracking parameters from website URLs.
Let me give you an example of what this is, in case you don’t already know. Suppose you’ve click on a link inside Facebook to an article somewhere else – maybe for techaddressed.com? The URL for that link might end up looking like this:
https://www.techaddressed.com/tutorials/gravity-sync-pi-hole-instances/?fbclid=IwAR2w-m1rASGVORDQN5jGHjbkGfOz4mxboWXadR7FXz8GKp9lOnumKOkpPJgFacebook and other sites will often append extra information onto URLs to allow them to track clicks. At this time, Firefox is only stripping additional parameters set by Drip, Facebook, HubSpot, Marketo, Olytics, and Vero. While it’s not exhaustive, it’s better than not having this feature at all.
Facebook isn’t perfect – they do collect a limited amount of data by default through what they call Firefox Suggest and a few other additional features that aren’t enabled by default. All of this is outlined in their actually easy to follow privacy notice.
The Firefox Suggest settings are easy to disable. In the Privacy & Security tab in the browser settings, disable the Suggestions From The Web and Suggestions From Sponsors options. Additional information on customizing these settings is available.
With the addition of a few add-ons that I discuss below, you can improve the privacy protection of Firefox even further.
TOR Browser
Tor Browser is a modified form of Firefox created by The Tor Project Inc – a registered non-profit group dedicated to open source anonymity and privacy technologies – and designed to access websites through the Tor network. Tor stands for “the onion router”. Onions have layers. Tor has layers.
The Tor network is composed of nodes run by thousands of volunteers around the world. Transmissions through the Tor network pass through three different servers in the network – each adding a layer of encryption – until it exits the network somewhere else entirely.
Think of it as a sort of VPN service built into your browser – servers on the other end of the transmission think you came from the node you where exited the TOR network. Anyone monitoring your browsing habits while using Tor browser realistically only know you’re using Tor and nothing else.
In addition to making use of the Tor network for encrypting and hiding all transmissions, Tor browser features additional data privacy and security features such as website isolation – preventing trackers from following you – and fingerprinting resistance due to all Tor traffic looking the same as all other Tor traffic.
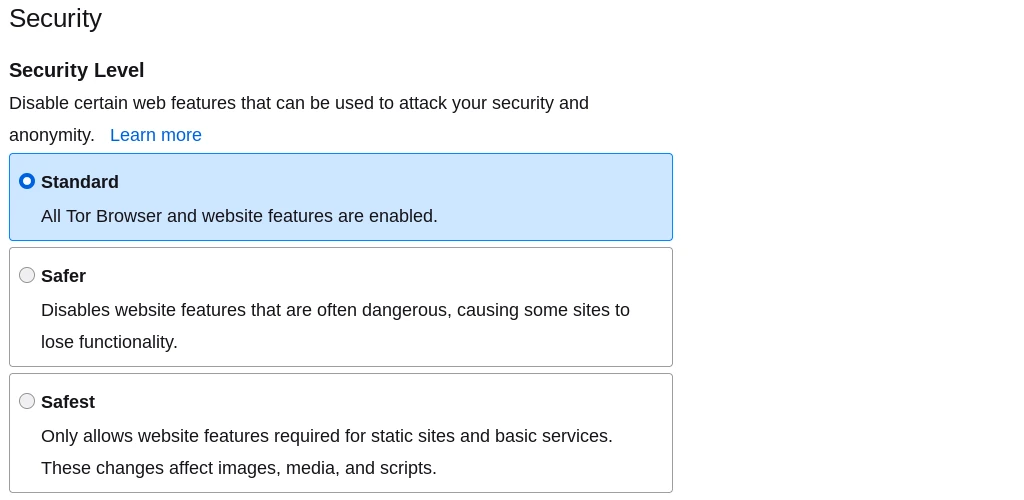
Tor browser’s security settings have three different options.
Changing the setting to Safer disables Javascript execution on any website not using HTTPS encryption, disables the use of certain fonts and math symbols, and enables click-to-play for on-page audio and video.
Changing the setting to Safest disables Javascript execution on all websites, disables the use of some fonts / icons / math symbols / and images, and enables click-to-play for on-page audio and video.
Tor browser comes bundled with a pair of extensions preinstalled: HTTPS Everywhere – which I discuss later in this section under “Helpful Browser Add-Ons / Extensions” – and NoScript – which it uses to handle the disabling of Javascript.
Tor browser’s default search engine is DuckDuckGo – which I discuss further in this article why you shouldn’t use DuckDuckGo at this point – however other options, such as Startpage, are preconfigured as options you can enable.
Keep in mind, if you happen to login to any sites or services while using Tor browser – say you decide to check a Gmail account – Google will know it’s you in that Tor session. They won’t be able to follow you around, however, they will know it’s you and will know you’ve made use of Tor.
Brave Browser
The Brave browser has some really compelling privacy features which make it seem like an obvious choice. It’s built on Chromium (the open source version of Chrome) but with all the Google-y bits pulled out – making it feel familiar to people who would normally use Chrome. However, Brave includes a number of privacy focused features like:
- Built in ad-blocking
- Cross-site tracker blocking
- Cookie blocking
- ‘Fingerprinting’ blocking
- Malware & fishing protection
- Protection from bounce tracking
- Anonymized network routing (Tor mode)
While many of these features are available in (or can be added to) other browsers, Brave enables them by default.
My only problem with Brave is one of personal convictions and not any technical or privacy reasons – which is why I’ve included it in this article even though I won’t personally use it. Brave is highly entwined with it’s own cryptocurrency. For the most part, I don’t support crypto currency as I see crypto mining as wasteful of electricity and and as a result it’s harmful to the planet. Bitcoin alone is estimated to use 127 terrawatt-hours of electricity per year – which is more than some countries.
Brave includes a built in crypto wallet for storing your crypto currency holdings as well as an option to earn “Brave Rewards” in the form of BAT or “Basic Attention Tokens” – their form of crypto coin that they pay you with for opting to view ads from their own first party ad-network.
You can decide for yourself whether this is the right privacy focused browser or not for you.
Problems With Chrome / Chromium / Edge / Safari
Now let’s discuss the browsers you’re most likely using and a little of why they’re problematic.
Near the start of this article, I mentioned that the Chrome browser gives Google information on what you’re doing online – even if the sites you visit aren’t using Google Analytics or any form of tracking, Chrome allows them to collect data on your browsing behavior. This, obviously, applies to ChromeOS as well.
You might think Chromium being open source would respect your data privacy, however, it too sends data back to Google. Complicating matters further is that Chromium does not automatically update itself like other browsers do – updates are left up to users to remember, creating a potential security nightmare
You might expect Chrome to be the worst offender when it comes to violating people’s data privacy, however, one computer science professor who published an in depth study on the matter concluded that Edge was the worst privacy offender. It’s not like Microsoft has a history of being trustworthy when it comes to privacy and security.
Apple doesn’t escape scrutiny either – while they don’t collect data quite like Google or Microsoft, they do collect some data on you for the purposes of targeted ads and there is the matter of being paid an $15 Billion+ per year to keep Google as the default search option on Apple devices – aiding Google in their efforts to collect as much data as possible on you.
For all of these reasons, I cannot recommend any of these browsers to people worried about protecting their data privacy.
Problems With DuckDuckGo Privacy Browser
As I mentioned below with regards to DuckDuckGo’s search engine – DuckDuckGo has long been a darling of the privacy conscious crowd, so news that they had a hidden agreement with Microsoft to allow their trackers to work while blocking trackers from the likes of Google and Facebook has caused quite a stir.
Because of this blatant deception and willingness to put aside the protection of people’s data privacy for money, I cannot recommend anyone to use DuckDuckGo.
Be Choosy About Add-Ons / Extensions
It’s been years since I directly supported user desktop PCs so I honestly don’t know what the current landscape is like when it comes to people’s browsers being overwhelmed with plugins, however, I remember well what things were like in the late 90’s and early 00’s and how many search bars and other various browser plugins would end up on the average person’s PC causing all manner of problems.
I hope we never know this nightmare again.
Browser add-ons / extensions aren’t necessarily bad in and of themselves, however not every one of them can necessarily be trusted so be careful about which ones you install. Browser extensions, like the apps on your phone, will often require you to grant them permissions. Look at what permissions each extension requests and consider whether they seem appropriate for what the software claims it will do.
Helpful Browser Add-Ons / Extensions
While keeping in mind my advice on being choosy about what add-ons and extensions you install in your browser, there are a few plugins that I can recommend without reservation.
EFF Privacy Badger
Privacy Badger from the Electronic Frontier Foundation is unlike any other privacy or blocking browser plugin – it learns what items to block by observing the behavior of resources that load with each page you visit and recognizes what resources are tracking you across multiple sites. When this happens, Privacy Badger will no longer allow your browser to load those tracking resources.
An interesting side effect you’ll notice with Privacy Badger is that it will block the vast majority of advertisements – but it isn’t actually an ad blocker. Ads often come with trackers bundled in with them. As a consequence of these trackers, the advertisements end up being blocked with them. This was setup this way by design as a way to try to incentivize ad networks to develop privacy friendly advertisements.
I highly recommend Privacy Badger for everyone who is even remotely worried about protecting their data privacy.
HTTPS Everywhere
HTTPS Everywhere is another plugin made by the Electronic Frontier Foundation. It’s job is simple – force all websites you visit to transmit via HTTPS – the encrypted form of the HTTP protocol. While most browsers have some level of built-in support for doing this already, HTTPS Everywhere is a bit more forceful.
Startpage Private Search
I talk about Startpage in the next section on privacy respecting search options, however, I’m mentioning them here as they offer a browser add-on for enabling their search in-browser. Keep reading for additional information on Startpage.
Privacy Respecting Search Options
There are some really great options available for searching the web without being logged or tracked in any way. A couple are even open source projects that you can host yourself (or just use one of the publicly available instances). Unfortunately, I need to point out that there’s a popular search engine that bills itself on protecting privacy but was recently (as of the time of publishing) exposed for this not being exactly true.
Recommended Options
I’ve included screenshots for search results of each of the options I recommend so you can compare them against each other to help you decide for yourself which you prefer.
SearXNG
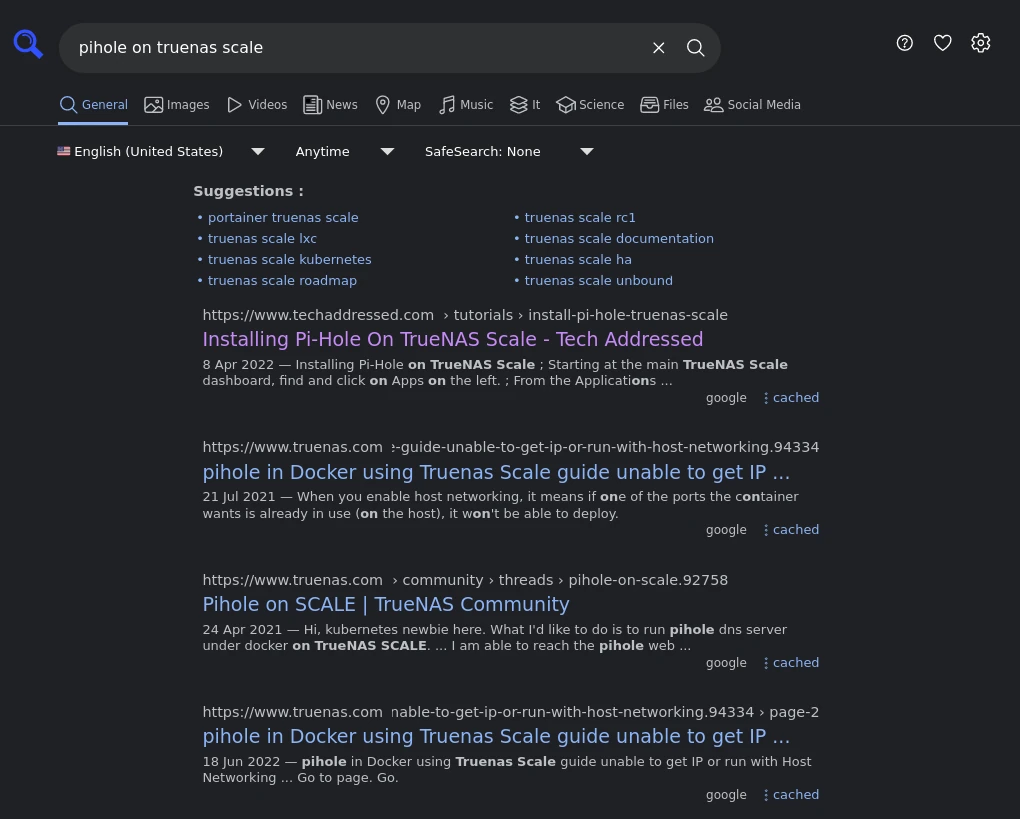
SearXNG only just came to my attention as I was researching this article but it has left me with such a great impression that I intend on writing a dedicated tutorial on setting up your own SearXNG instance soon. For those interested in self hosting, I’ll update this article with links once that tutorial is complete.
SearXNG is what’s known as a metasearch – it aggregates results from multiple search engines together into a single result. If you look closely in the screenshot above, you’ll notice how it says under each result that it pulled these results from Google, however it’s possible to get results back from a combination of sources.
When SearXNG performs searches, it separates you from all of the searching so Google, Bing, etc… don’t have any indication of who you are or your IP or anything. All cookies, scripts, and nasty privacy invasive stuff is stripped out in the process of putting the results together for you.
If you’re not interested in setting up your own instance of SearXNG you’re still in luck – there are over 80 instances setup and made public by generous individuals out there.
Startpage
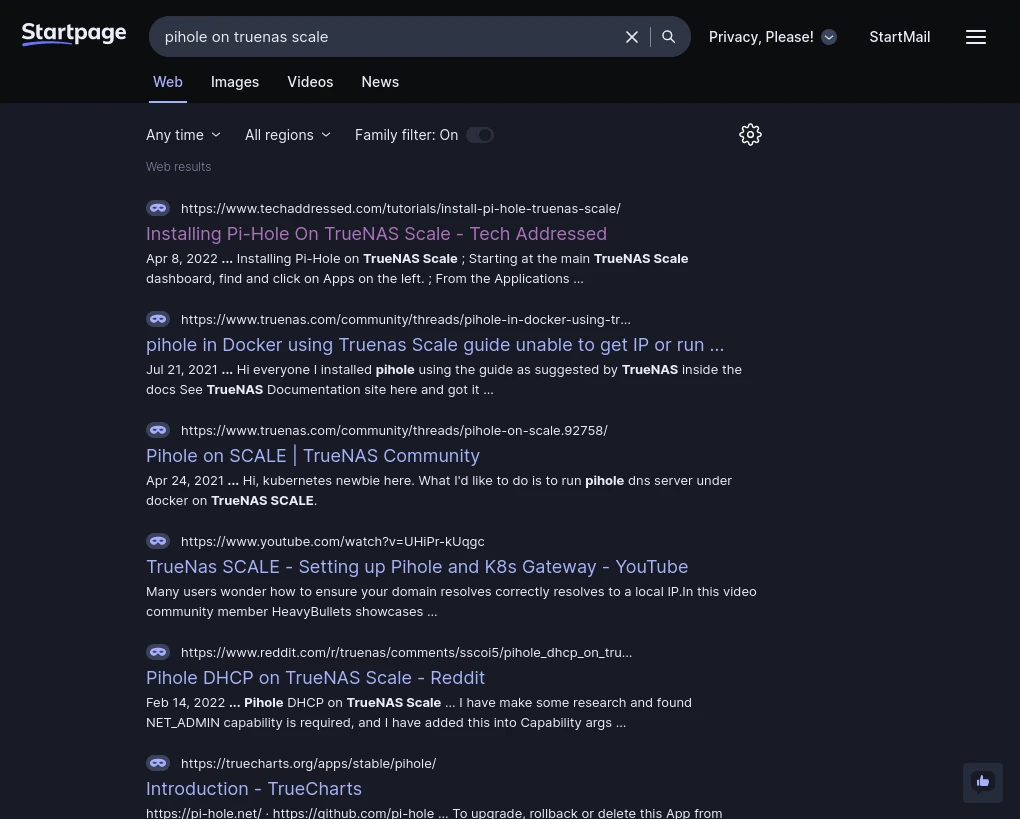
Startpage is a company based in the Netherlands that produces privacy focused technologies including their search site, a search plugin (mentioned earlier) for your browser, and a private email service (mentioned in the next section of this article).
Being based in Europe, Startpage is subject to GDPR so you can expect them to take your privacy seriously. One interesting feature their search includes that you won’t find elsewhere. If you look at the search result screenshot above you’ll notice each result has a small mask icon next to the URL of the result. Clicking on this URL will browse to that result in what Startpage calls “Anonymous View” – essentially acting like a no cost VPN that doesn’t require you to create an account to use.
Whoogle
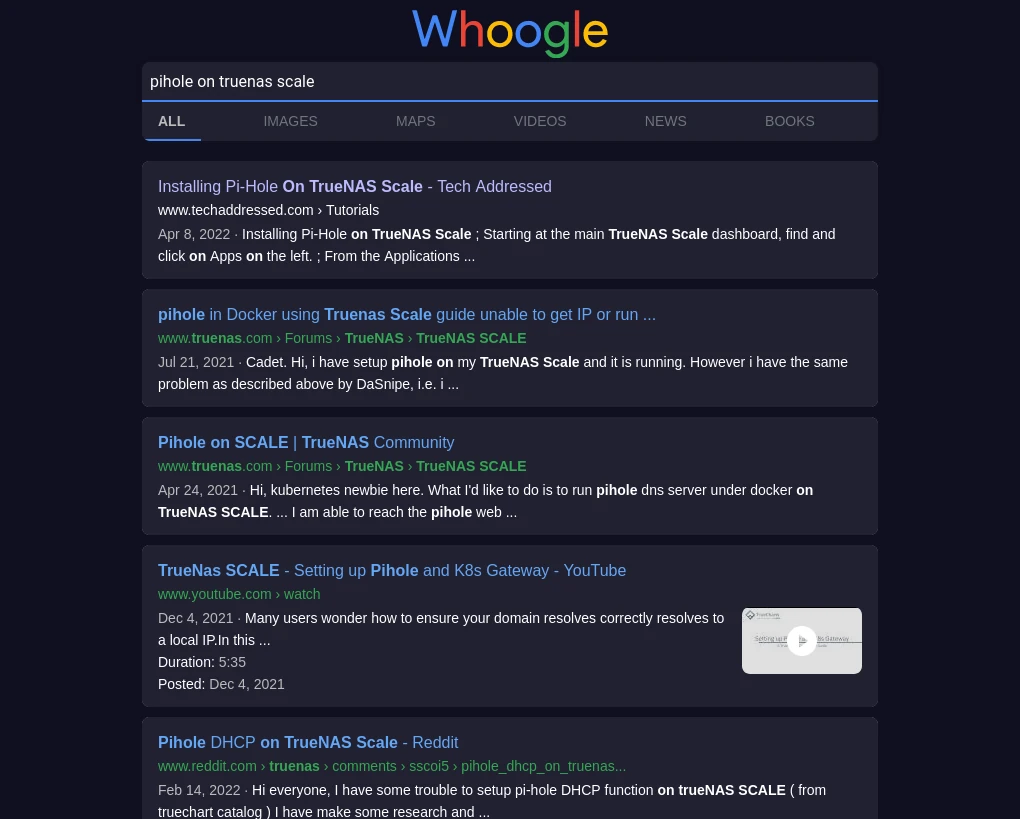
The last of the private search options I’d recommend is one I’ve been using myself for a while now called Whoogle. I recently published an article on deploying your own self hosted Whoogle instance – for those who are interested in setting up their own.
Like SearXNG, Whoogle is an open source project. Unlike SearXNG, Whoogle is not a metasearch – it only performs anonymous Google searches. It’s important to note that Google sees the IP address of wherever the Whoogle search is hosted from so if you intend to setup your own, you’ll want to be sure to host it on a cloud based server somewhere so that it doesn’t use your home IP address.
Examples of such providers – Linode (affiliate) / DigitalOcean (affiliate). If you want to be extra careful about your choice of cloud host, Exoscale is based out of Switzerland. I can personally vouch for both Linode and DigitalOcean but I haven’t (yet) used Exoscale but plan to check them out soon.
Problems With DuckDuckGo
As I mentioned previously with regards to DuckDuckGo’s browser – DuckDuckGo has long been a darling of the privacy conscious crowd, so news that they had a hidden agreement with Microsoft to allow their trackers to work while blocking trackers from the likes of Google and Facebook has caused quite a stir.
Because of this blatant deception and willingness to put aside the protection of people’s data privacy for money, I cannot recommend that anyone use DuckDuckGo.
Privacy Focused Email Services
Privacy centered email services where messages are securely transmitted and stored – especially when they’re hosted in privacy respecting countries – are invaluable for protecting your data privacy.
Recommended Options
There are three privacy focused email providers I recommend – one has a free option, two are based in Switzerland while the third is in Germany, and two have anonymous payment options. Each has various options that differ from the other – choose the one that fits your data privacy needs best.
Proton Mail (Affiliate)
Proton Mail is offered by the same Switzerland based company that runs Proton VPN (mentioned previously) and Proton Drive (mentioned below). They offer a limited free plan along with Plus and Premium plans (affiliate) with prices ranging up to 10€ per month.
Plus and Premium plans come bundled with greater storage space and additional services – the Premium plan even includes VPN service.
As you might expect, Proton Mail is fully encrypted – both in transit and at rest – and is protected by Swiss data privacy laws. There’s very little not to like.
Posteo
Posteo is a mail service from Germany that takes privacy seriously. While they don’t offer a free service, their services are very affordable. They have only a single plan that costs 1€ per month.
Posteo goes an extra step in protecting your privacy by decoupling your payment from your account information. All payments are anonymous. Posteo has you add credit through either sending them cash via the mail, payment via bank transfer, payment via PayPal, or you can opt to pay using a credit card. Payment must equal at least one year of service, or 12€. Exact details of this are provided during account setup.
No matter which payment method you choose, however, your account is active immediately after you complete registration – restrictions are in place on unpaid accounts to guard against abuse / spammers. Account registration collects no personal information about you at all.
If you’re ecologically minded – Posteo boasts that they’re powered 100% by renewable energy.
Most importantly, all data is easily encrypted “with the touch of a button”.
StartMail
The last email service I recommend is StartMail offered by the same team behind Startpage private search.
StartMail isn’t quite as affordable as the previous two options though it’s still reasonable – they do offer a free seven day trial period as well.
Depending on which of their two plans you choose – you have the option to choose to use a custom domain instead of theirs for an extra fee – the normal price is between $5 and $6 per month (billed annually).
As you would expect, all messages are fully encrypted.
Encrypted Messaging
The importance of having protected communication options cannot be overstated and there are a couple good apps out there you can use for this purpose. Though, much like we’ve seen with certain search options having an undeserved reputation for protecting data privacy, this there is a messaging app that I’ll discuss that does not deserve the recommendations it gets from others as being private.
Recommended Options
A large amount of the information used to compare messaging apps came from securemessagingapps.com – which I mention so you too can look at the easy to use comparison chart provided there to help make your decision on which apps to use. Out of all of them, I’ll only personally recommend two.
Session
Why use Session? Among other things – It’s free. You can sign up anonymously. It doesn’t collect any of your data nor send data to any third parties. It’s open source and fully encrypted.
Any down sides to Session? Generally speaking there’s very little to worry about with using this app.
Signal
Why use Signal? Like Session, it’s free to use. The only data collection is your contact information and mobile number (used for account recovery). It’s open source and fully encrypted. Is more well known than the other apps mentioned here – possibly making it easier to convince others to use it or find others that already do.
Any down sides to Signal? You cannot create an account 100% anonymously – your mobile phone number is required.
Problems With Telegram
The Telegram app is often thought of as a secure messaging platform because it was one of the first such apps available with end-to-end transmission encryption. However, there are a number of concerning details about Telegram that users should be aware of and why I and many others would never recommend using it if data privacy or security were important considerations. These are only a few:
- Custom / non-standard encryption methods
- Encryption not enabled by default
- Company collects user data
- Company can read your messages
For those who aren’t versed in cryptography, using custom encryption methods is generally frowned upon as the methods haven’t been reviewed for flaws or vulnerabilities and therefore isn’t something that should be trusted to secure important data. Standards exist for a reason.
The rest of the issues mentioned should be fairly straight forward – and like I mentioned, these are only a few of the problems with Telegram.
Encrypting Your Devices
While not every device / operating system enables encryption by default, all of them have the ability to be encrypted.
Windows
Disk encryption for Windows is possible but to the uninformed it could be a bit confusing. Microsoft offers two versions of the same technology for encrypting your PC’s drives – Device Encryption and BitLocker Encryption. So why two versions of the same thing?
Most people’s PCs have the Home edition of Windows as opposed to the Pro or Enterprise versions. The Home edition only has the option to use Device Encryption and cannot use BitLocker and ONLY if you login to your computer using a microsoft.com account – it will not work with an account that is only local to your PC.
The reason for this is that your microsoft.com account is associated with a OneDrive account and they store a recovery key in that account because they don’t trust that you won’t accidentally get locked out of your encrypted computer. While I can see that this is probably helpful for some people, it also means that a key exists for unlocking your encrypted disks that you have zero control over and could be turned over to authorities if requested.
If this is a concern for you, my suggestion would be to upgrade your Windows edition to a Pro license instead of a Home license – which would allow you the option to use BitLocker instead which doesn’t have these issues.
Other suggestions would be to consider encrypted cloud based storage for your files instead of storing them locally on your computer or switching from Windows to something more privacy respecting like Linux.
MacOS
Compared to Microsoft, Apple at least treats you like an adult if you intend to encrypt your Mac using FileVault. During the setup, you’re offered a choice of whether to unlock your startup disk in the event you forget the encryption password – either via your iCloud account username/password or through the creation of a recovery key that you’re responsible for keeping somewhere safe. I would recommend against using your iCloud account and instead create a recovery key.
Linux
With as many different Linux distributions that exist, I can’t exactly provide definitive links on any one way to setup disk encryption. Some distributions make it available to setup disk encryption as part of the system installer. It’s always possible to encrypt after the fact. Either way, the technology you’re likely using to encrypt your disk is something called Luks.
I trust that most Linux users will know how to find documentation for their distro on how to get your disks encrypted and if you need help I know there are forums that exist with people who would be willing to help – example: Level1Techs Forums.
ChromeOS
Chromebooks and other Chrome OS devices are fully encrypted by default. The only way to access any files stored on them is with access to your Google account which is required to login to the device. This is great for your data privacy were someone were to steal your Chromebook, however, Google can be compelled to unlock your device via a court order.
Android
Virtually all Android phones sold in the last few years have encryption enabled by default. This encryption is protected by your phone’s authentication. If you someone can get past your lock screen, they have access to everything so be sure to follow my advice above about strong passwords.
It’s important to note that your Android device does not automatically encrypt any micro SD cards you add to your device. If you’ve added an card, you’ll need to enable encryption on it yourself. If you encrypt your SD card do be aware that it can ONLY be used on the exact same phone that encrypted it. If you remove the card and attempt to read it in another device it will not work.
iOS
Apple iOS devices automatically enable encryption as soon as you setup either a face ID or passcode for your device. There are some important caveats to remember here, however. First, you have to jump through a couple minor hoops to set an actual password instead of just a numeric pin.
Second, as I mentioned near the top of this post – while Apple had planned to encrypt backups stored on iCloud but scrapped that plan after objections from the FBI, they did eventually come around and provide this feature. It isn’t enabled by default but it is available.
Apple’s better than most, but don’t treat their data privacy stance as an absolute.
Cloud Storage Providers
As I’m hoping you’ve realized by this point – where your data is stored is directly related to how private your data is. Anything stored in Google Cloud, Dropbox, or iCloud – for example – is easily obtained by a government authority with a subpoena. If you need cloud based storage, then, where do you turn to?
Recommended Options
There are MANY cloud storage providers based in Switzerland. I’ve chosen two to present to you here. If you aren’t satisfied with either of these, you won’t have a hard time searching for others.
pCloud (Affiliate)
Switzerland based pCloud is a data privacy focused provider of cloud based file storage boasting over 16 million users. All data is fully encrypted with the option to upgrade your plan for additional protection.
The offer a number of advanced features including file versioning, collaboration capabilities, ability to sync across multiple devices, and even built in video and audio players.
Plans ranging from 500GB to 10TB of space are available with options for monthly, yearly, and one-time lifetime billing.
Proton Drive
If you can’t guess by this point, Proton Drive is from the same Switzerland based company behind Proton VPN and Proton Mail.
They offer a limited free plan along with Plus and Premium plans with prices ranging up to 10€ per month. Plus and Premium plans come bundled with greater storage space and additional services – the Premium plan even includes VPN service.
As with all of their services, everything is fully encrypted – both in transit and at rest – and is protected by Swiss data privacy laws.
Advanced Tools
It’s entirely possible to protect your data privacy without having to consider any of these advanced tools mentioned here. However, if you are really interested in taking things up a notch there are a few things you could consider.
Running a Tor Network Relay
Contributing to the Tor network by running your own relay on the network is one way to give back to everyone else who relies on the network to ensure their data privacy. This isn’t something someone afraid of technology should take on but knowing you’re helping protect other people is rewarding.
Linux
I know this one is asking a lot of most people – but I can dream, can’t I?
If you want to be 100% certain that your computer is not collecting data on you to send back to Microsoft / Apple / Google – you should consider using one of the many Linux distributions instead. Which one is up to you, but if you want something easier to use while you’re new to Linux I’ll make three recommendations:
I don’t have space here to go into details of how exactly to do this but I do plan to create tutorials on this in the future which I will link back here when they’re available. In the meantime, there are countless tutorials on the web and on YouTube that you can use to help you.
Tails
The last advanced tool I’ll mention is actually another Linux distribution – Tails. Tails is a Linux distro that you don’t install to your computer directly but instead use by booting to a USB flash drive and is designed with with protecting data privacy in mind.
Every time you boot to your Tails drive, you start with a clean slate – it doesn’t remember any of the websites you’ve visited or the files you’ve opened, though it is possible to store some data in persistent storage if needed. All files in persistent storage are encrypted.
Tails comes preconfigured with tools such as Tor Browser and KeePassXC – an open source local password manager. All applications are blocked from communicating with the internet without connection to the Tor network.
If you’d like the data privacy benefits of Linux without having to nuke the operating system from your computer, consider giving Tails a try.
Conclusion
The scope of this article kept growing as I wrote it – originally I expect it to be roughly half this size – so I hope that I’ve covered everything necessary. It’s my sincere hope that the information here helps as many people as possible better improve their personal data privacy. As I mentioned in the opening of this article, if you have any comments or suggestions or questions, please comment below or reach out to me via social media. All constructive feedback is welcome.
If you found this article helpful, I encourage you to please share it with others who can use it as well. If you would like to support our efforts to create additional resources like this, please consider making a donation. Your support is greatly appreciated! Thanks for reading. Stay vigilant. Stay safe. I hope you visit again soon.